Overview
The goal of this crackme is to find out what password(s) make the program print out Password OK :).
We ended up looking at the Windows binaries only.
Write-up
crackme0x00
Takes input through scanf and performs quick strcmp with string 250382 from strings table.
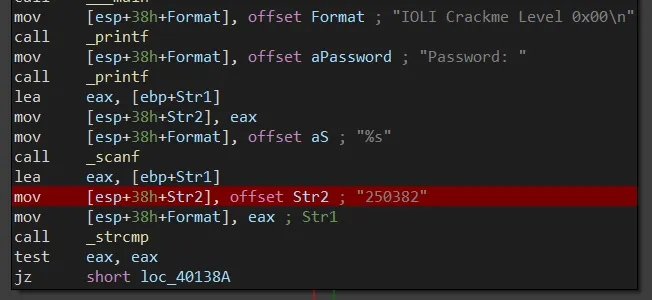
Password: 250382
crackme0x01
As above but strcmp with integer 5274 read by scanf instead.
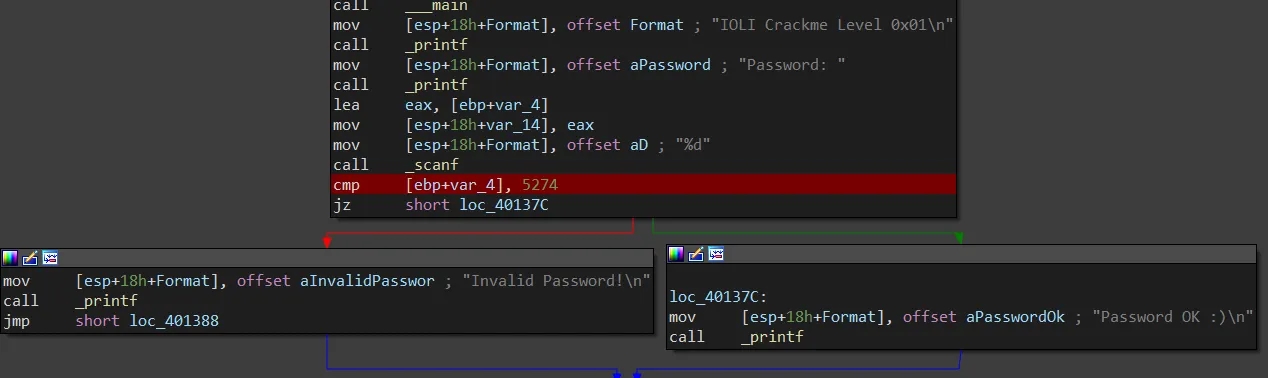
Password: 5274
crackme0x02
scanf input is read and stored as integer. We then perform some arithmetic which ends up adding two integers (90+492 = 582) before doing the multiplication 582*582=338724. Finally, our scanf_input and this value is compared.
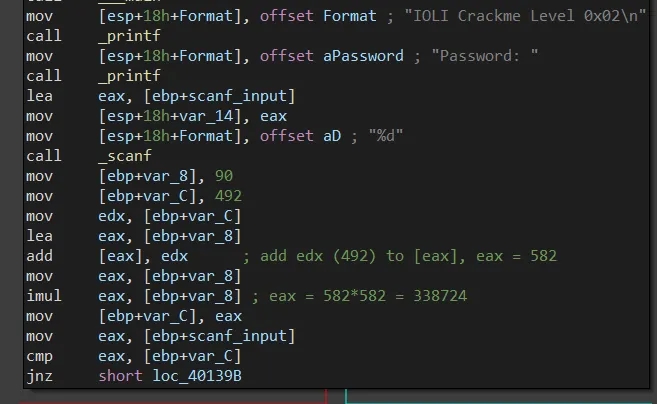
Password: 338724
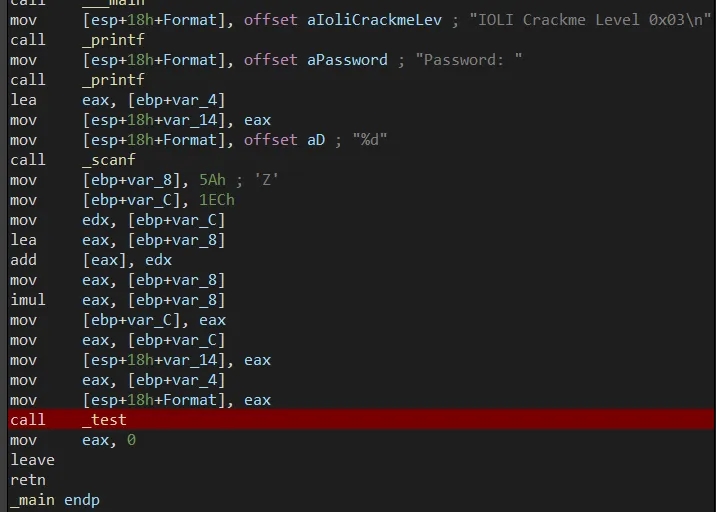
crackme0x03
The final comparison logic is now moved into a _test subroutine. No other behaviour has changed and our password from the previous level is still valid. However, we notice the Password OK!!! :) and Password Invalid! strings are no longer present and instead we see some cipher text which looks like Lqydolg#Sdvvzrug$ and Sdvvzrug#RN$$$#=,. This is because they have been encoded with a cipher and the _shift subroutine deciphers the ciphertext before they are printed using printf. The cipher is a simple ASCII Caesar shift with a shift of 3.
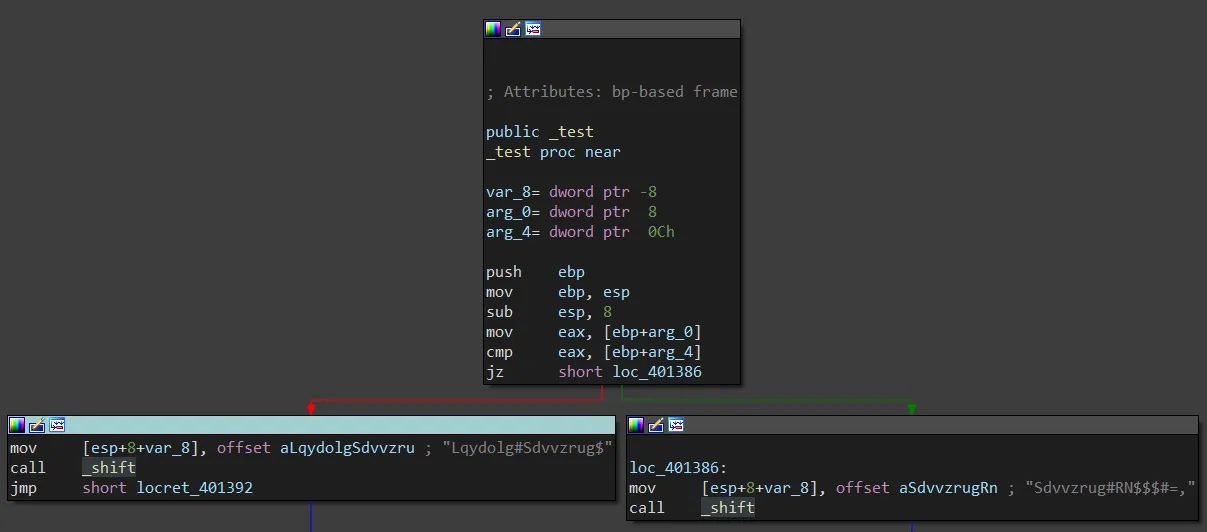
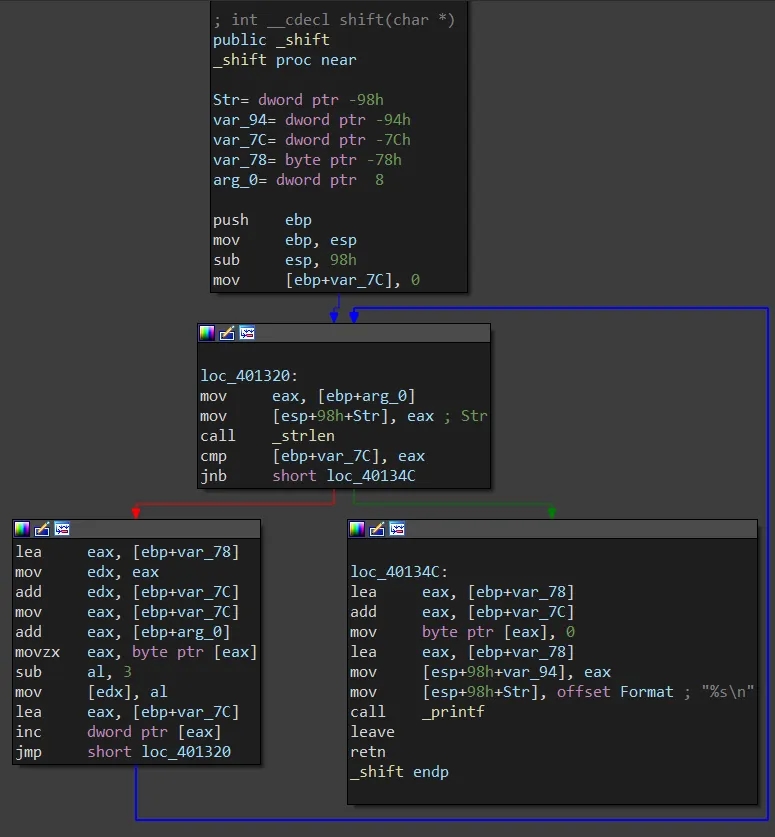
Password: 338724
crackme0x04
All of the interesting functionality is inside a check subroutine which our input_pass_string is passed to. The sub iterates over the input string and performs a sscanf call which attempts to parse each character as an integer (%d format identifier). Each digit value is then added to some total integer before being compared with the integer value of 15. Therefore, our input can be any sequence of digit characters that sum to 15.
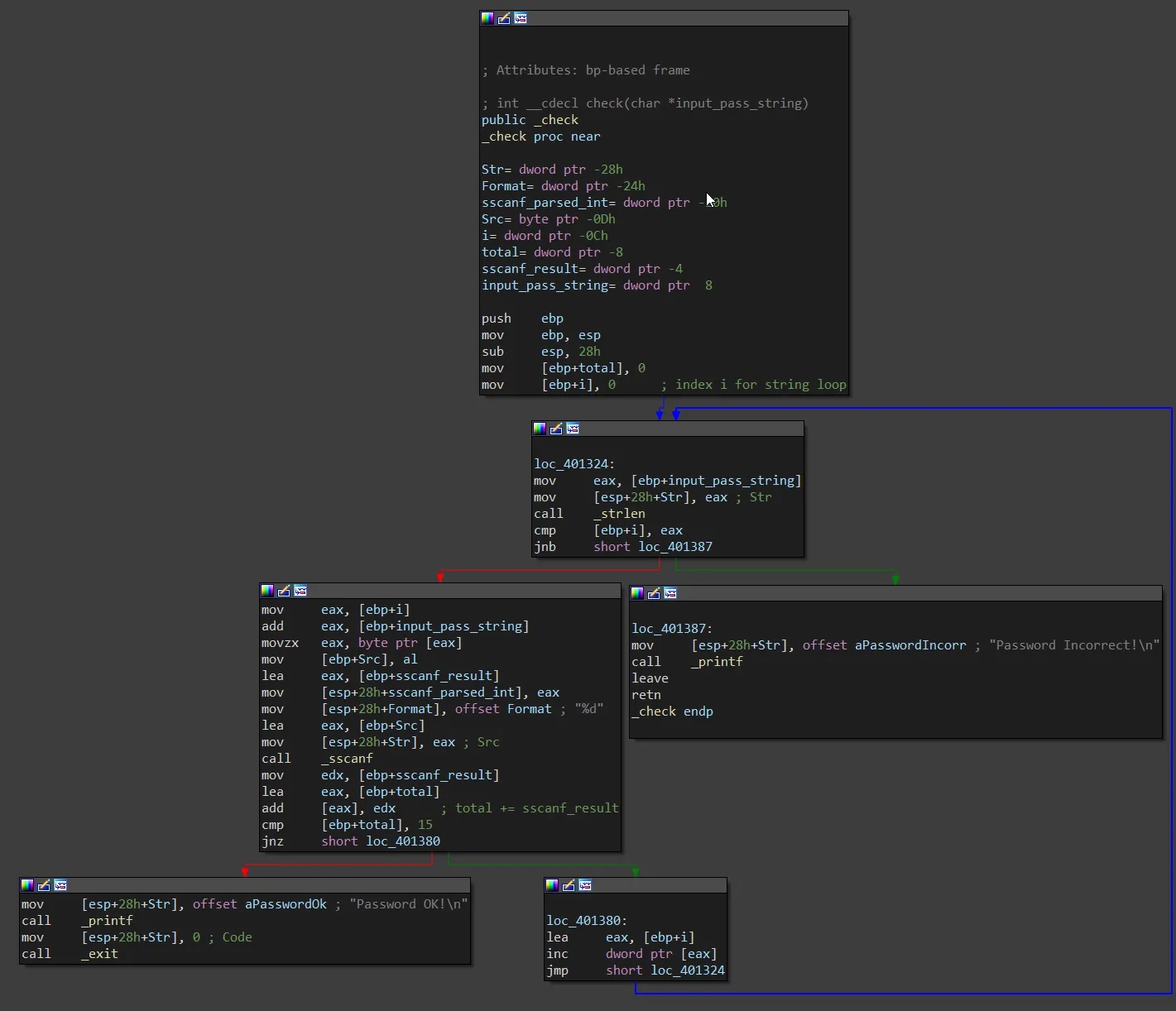
Password: Any sequence of digit characters that sum to 15. (i.e. 96, 76, 78, 87, 69, 555, 111111111111111).
crackme0x05
Same as 0x05 except compare value is now 16 instead of 15 and one final check is done in the new _parell sub.
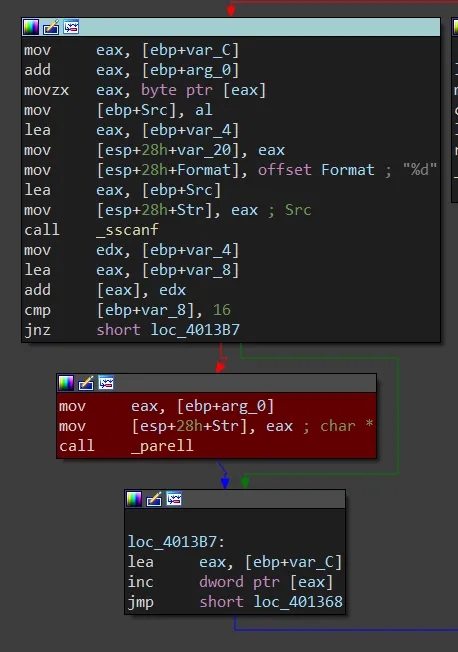
This final sub simply takes in a character, converts it to a digit then performs the following two operations on it:
and eax, 1
test eax, eaxTo reach the Password OK branch we need the test instruction to set the zero flag. This will only happen if EAX is 0 when the TEST instruction is executed. For this to be the case, the original EAX value which was used in the AND instruction with the immediate value 1 must have a least significant bit of 0. In other words the sscanf_digit must be an even number.
As this sub is only called once the original conditions are met (total value having a value of 16) our input simply must end with an even digit.
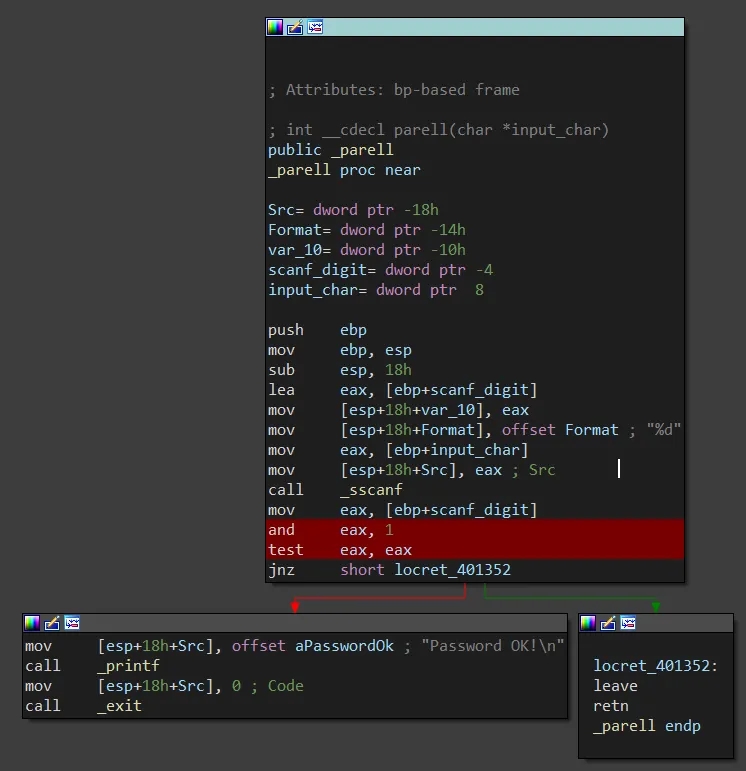
Password: Any sequence of digit characters that sum to 16 where final digit is even. (i.e. 916, 556, 111111111111112).
crackme0x06
Same as 0x06 except we notice that envp is passed down to our check sub from the entry point. This assembly suggests the original source code had a main function that took in a third argument:
int main (int argc, char *argv[], char *envp[])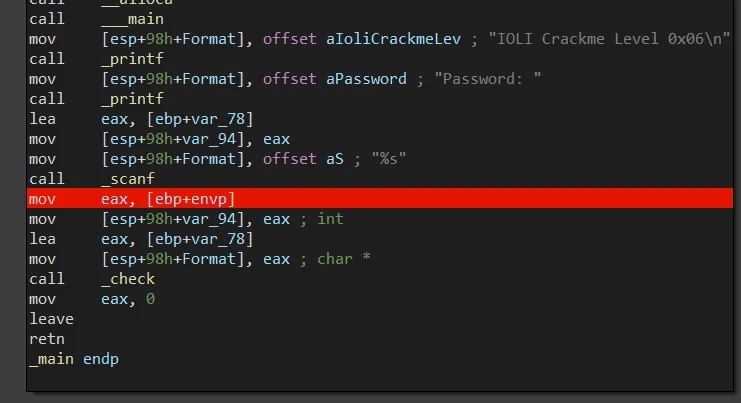
The array of pointers to the programs environment variables are passed to this dummy sub. In this sub we traverse the array of pointers and call strncmp with every environmental variable and the string LOLO with a MaxCount of 3. Note that environmental variables are strings in the form of MYENV=1. Therefore, we are simply iterating the environmental variables to see if any start with the string "LOL" (due to 3 character MaxCount).
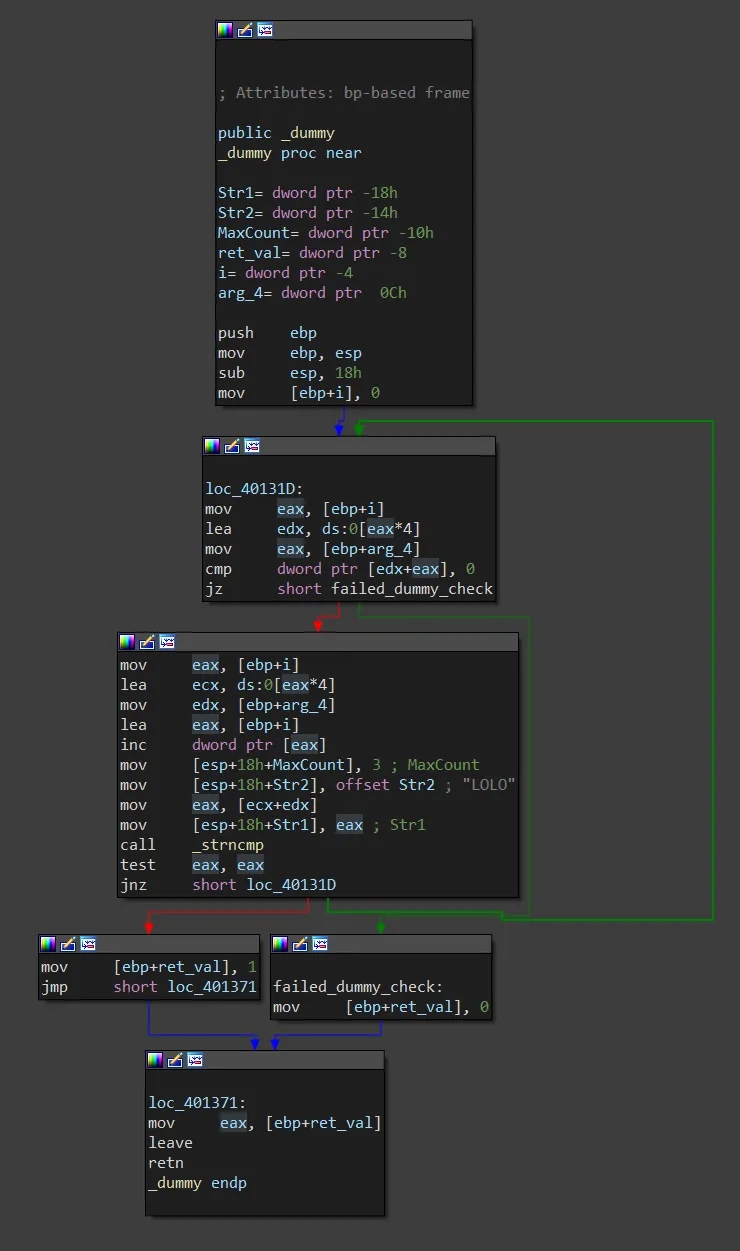
Password: Any sequence of digit characters that sum to 16 where final digit is even. (i.e. 916, 556, 111111111111112). Requires environmental variable that starts with string "LOL" to be set.
crackme0x07
Same as 0x07 functionality wise. However, we now have a windows application that enters via the WinMain entrypoint in console mode.
We also have a code segment in memory that is unreferenced. It seems as if this code block prints "wtf?\n" and leaves if the length of the input password is more than 9 characters long.
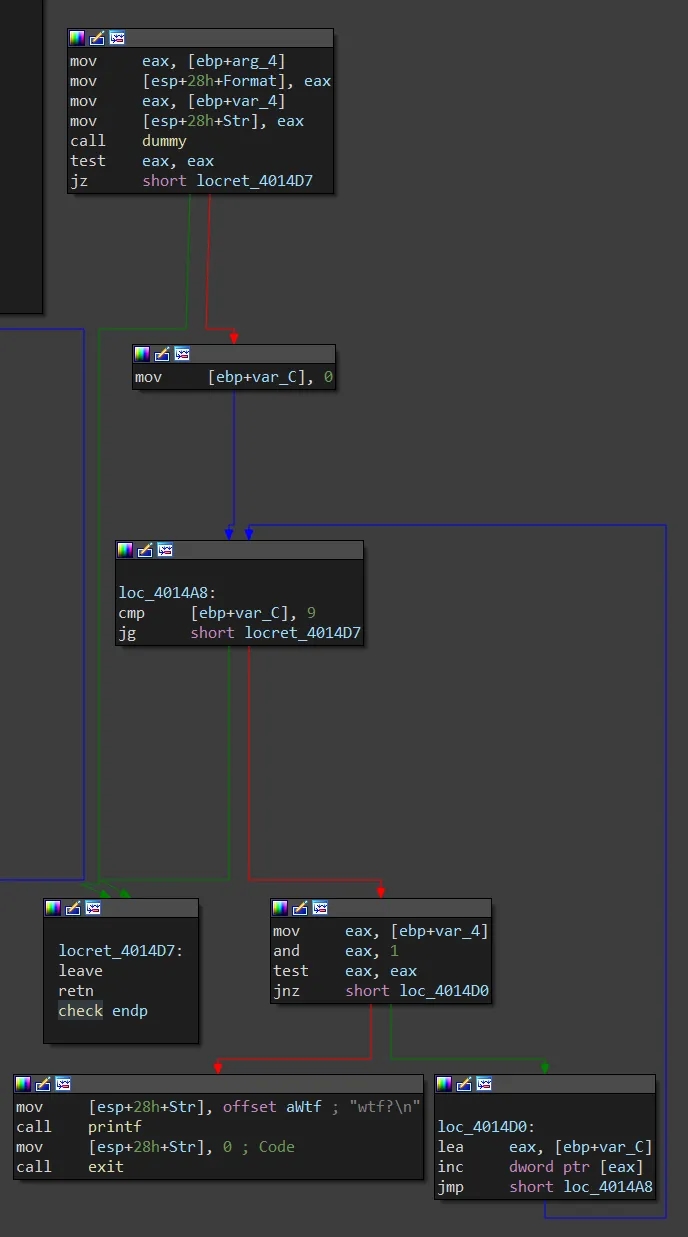
Password: Any sequence of digit characters that sum to 16 where final digit is even. (i.e. 916, 556, 111111111111112). Requires environmental variable that starts with string "LOL" to be set.
crackme0x08
Exactly the same as 0x07 but executable contains embedded pdb debug symbols which make reversing much easier. (File size gives this away also).
Password: Any sequence of digit characters that sum to 16 where final digit is even. (i.e. 916, 556, 111111111111112). Requires environmental variable that starts with string "LOL" to be set.
crackme0x09
Exactly the same as 0x07 except binary hashes are not identical but have the same exact byte size. Most likely just the same source code recompiled with no/very minor changes.
Password: Any sequence of digit characters that sum to 16 where final digit is even. (i.e. 916, 556, 111111111111112). Requires environmental variable that starts with string "LOL" to be set.