Overview
The Mashable subscription script has a flaw where it doesn't properly sanitize the email field, allowing an invalid email address to be displayed directly on an error page.
This oversight can be exploited by injecting malicious code into the email field, potentially leading to a Cross-Site Scripting (XSS) attack. For instance, an attacker could create a URL that runs harmful JavaScript in the user's browser, opening the door to session hijacking, data theft, or other malicious activities.
To prevent issues like this, it's essential for developers to validate and sanitize all user inputs. In this case, ensuring that the email input is properly filtered and encoded before it's shown on the error page would block XSS attacks.
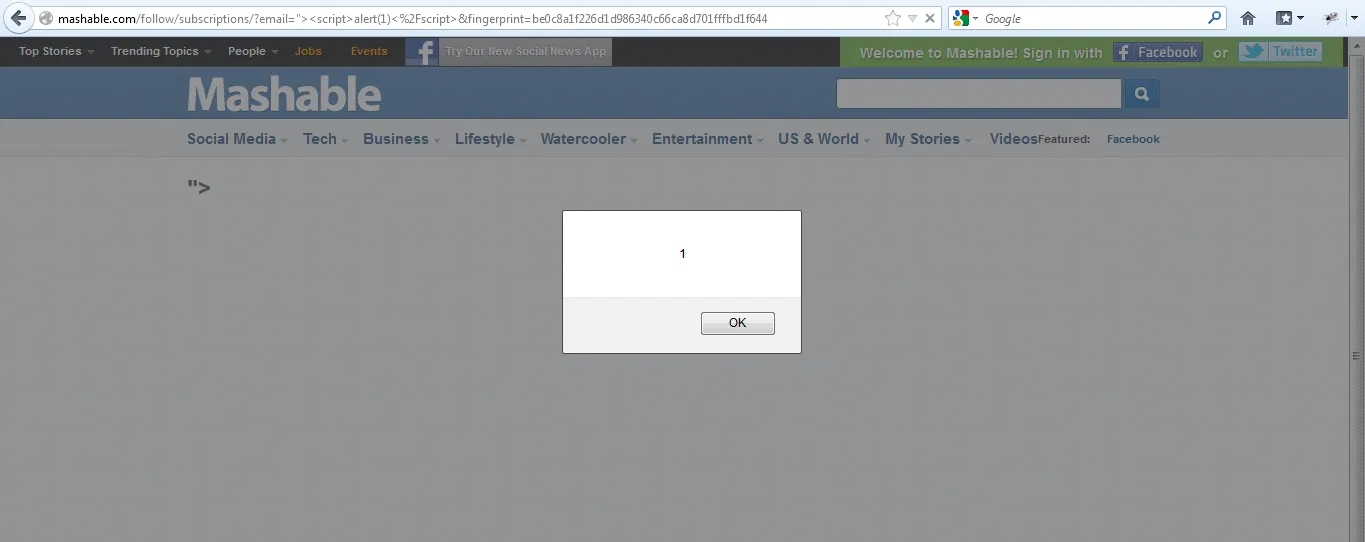
Vulnerable URL:
http://mashable.com/follow/subscriptions/
?email="><script>alert(1)</script>
&fingerprint=be0c8a1f226d1d986340c66ca8d701fffbd1f644