Overview
The SSL Server Test by Qualy's SSL Labs is an easy way to determine how secure your SSL set up actually is.
You can run the test at: https://www.ssllabs.com/ssltest/
This is the score for this domain/server:
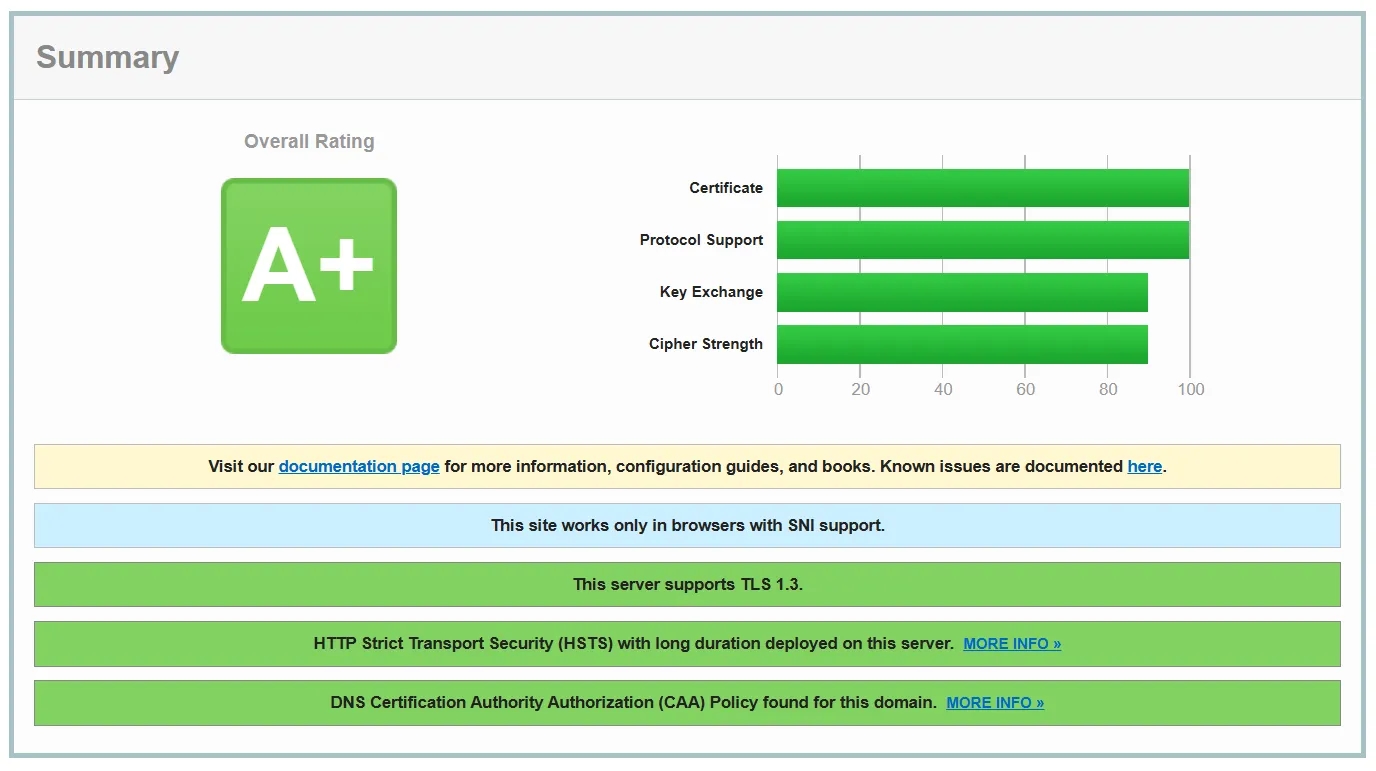
Getting an A+ score
The default Apache configuration for websites running HTTPs leaves your set up vulnerable to a variety of attacks. So you will need to modify the configuration file for your SSL enabled website.
First navigate to the httpd.conf file and open it in your favourite text editor. In my case this file was located at: /etc/httpd/conf
vim /etc/httpd/conf/httpd.confNavigate to the VirtualHost line that corresponds to the SSL enabled website.
Here is where we add all on configuration options. I'm not going to explain what each option does but do research that if it interests you.
The important configuration options we set are: SSLProtocol (disable SSLv2 and SSLv3), SSLHonorCipherOrder (Beast attack), SSLCipherSuite (support wide range of secure protocols) and HTTP Strict Transport Security. Obviously, replace the placeholder paths, server name (example.com) and file names.
<VirtualHost *:443>
SSLEngine on
SSLProtocol all -SSLv2 -SSLv3
SSLHonorCipherOrder on
SSLCipherSuite "EECDH+ECDSA+AESGCM EECDH+aRSA+AESGCM EECDH+ECDSA+SHA384 EECDH+ECDSA+SHA256 EECDH+aRSA+SHA384 EECDH+aRSA+SHA256 EECDH+aRSA+RC4 EECDH EDH+aRSA RC4 !aNULL !eNULL !LOW !3DES !MD5 !EXP !PSK !SRP !DSS !RC4"
SSLCertificateFile /var/www/example.com/ssl/www_example_com.crt
SSLCertificateKeyFile /var/www/example.com/ssl/www_example_com.key
SSLCertificateChainFile /var/www/example.com/ssl/www_example_com.ca-bundle
Header always set Strict-Transport-Security "max-age=63072000; includeSubDomains"
ServerAdmin webmaster@example.com
DocumentRoot /var/www/example.com/public_html
ServerName example.com
ServerAlias www.example.com
ErrorLog /var/www/example.com/error.log
CustomLog /var/www/example.com/requests.log combined
</VirtualHost>